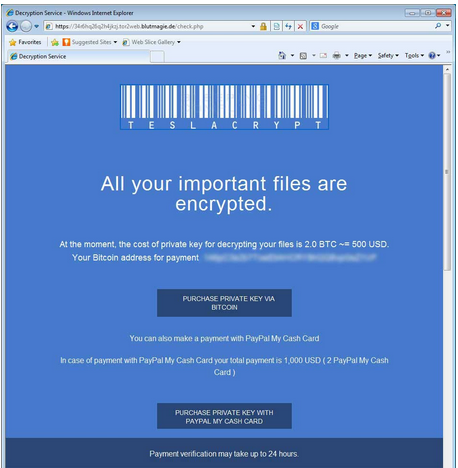
TeslaCrypt A New Ransomware For Gamers
- Published in Security
Rather than bombard you with all of the new ramsomware versions that come out (after the success of CryptoLocker there have been far too many copycats to mention) we've attempted focused on the new versions that are deviating from the standard either because there are work arounds or their targets / delivery are unusual. This week brings us one of those unusual cases...
TeslaCrypt has been discovered by Fabian Wosar of Emsisoft; TeslaCrypt is unusual because it is very specifically targeting over 40 different video game related files. The target games include, MineCraft, Call of Duty, World of Warcraft, RPG Maker, World of Tanks, Dragon Age, League of Legends, StarCraft, and Steam.

Most ransomware, prior to TelsaCrypt, has targeted images, documents, and videos.
Another interesting change with TeslaCrypt is for the first time we're seeing PayPal My Cash cards being accepted for the ransom payment. PayPal My Cash cards can be purchased at CVS, Dollar General, RiteAid, Family Dollar and Freds. After purchasing the card you login to your PayPal account and using the PIN on the back of the card apply the funds to your account.
Paying with a PayPal My Cash card is more expensive than paying with Bitcoins - $1000 vs. $500 USD. This is likely for two reasons, the first is using PayPal they are risking having PayPal confiscate their ill-gotten gains and second if you've ever tried to purchase Bitcoins it's not that simple and takes several days. So if you want to get your files unencrypted now you might pay the premium through PayPal. The latter would seem to work best in the case of a mission critical business server, but if you have the money and just can't stay away from World of Warcraft it might work on you too.
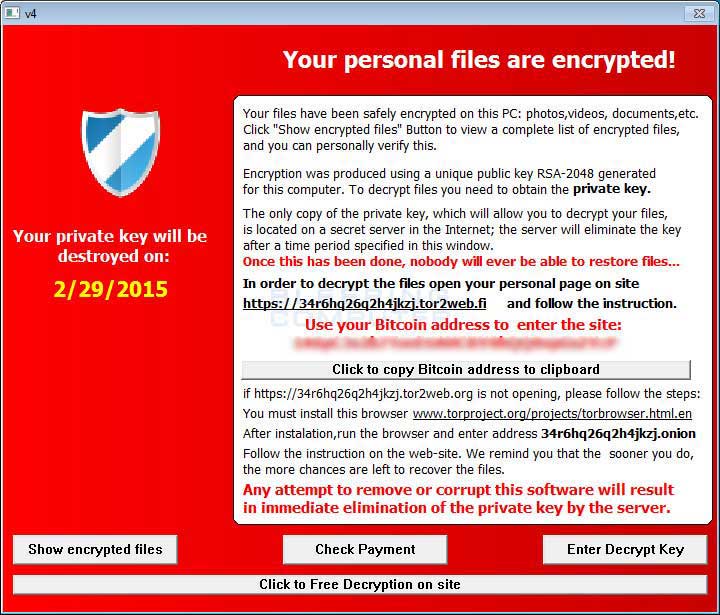 Image courtesy of Bleeping Computer
Image courtesy of Bleeping Computer
Like so much of the ransomware the standard red screen with a shield on the upper left is used to let you know your computer is infected.
Where the name TeslaCrypt came from is anyone's guess, although it is a name they gave themselves, see the screenshot. Perhaps they are hoping to be as successful as Tesla.